I remember the early days, not so long ago, when we first started migrating our clunky, on-premise ERP system to the cloud. It felt like we were moving from a fortress with a single, massive drawbridge to a sprawling, modern city where every building had its own intricate security system. The excitement was palpable – the promise of flexibility, scalability, and innovation was intoxicating. But beneath that gleaming veneer of progress, a quiet, yet profoundly important, challenge emerged: managing who could access what, and how, within this new, boundless digital landscape. This, my friends, is the story of ERP Cloud User Access Control, a tale less about technology and more about trust, responsibility, and the delicate art of balancing openness with security.
For those new to this world, let’s set the stage. ERP, or Enterprise Resource Planning, is essentially the central nervous system of a business. It’s where all the critical information lives – financial records, customer data, inventory, HR details, supply chain logistics, you name it. When we talk about "Cloud ERP," we’re talking about taking that powerful system and hosting it not on servers in your office basement, but on remote servers managed by a third-party provider, accessible via the internet. It’s like moving your entire company’s brain into a highly secure, shared data center somewhere out there in the digital ether.
Now, imagine that brain. It holds secrets, strategies, and the very lifeblood of your operation. Who gets to see which part of it? Who can change its memories? Who can add new information? That’s where User Access Control steps in. In simple terms, it’s the process of defining and managing what authenticated users are permitted to do within an ERP system. It’s not just about letting people in (authentication), but about controlling what they can do once they’re inside (authorization). When your ERP lives in the cloud, this aspect becomes exponentially more complex and critical.
Why, you might ask, is this so much more important in the cloud? Well, in the old days, physical security provided a layer of comfort. Your servers were locked away. If someone wanted to get to them, they had to physically break in. With Cloud ERP, the "physical" boundary is gone. Access is granted over the internet, from anywhere, at any time. This incredible flexibility, while a huge advantage, also opens up a vast attack surface. Every user, every device, every connection becomes a potential doorway. And this is where my journey into the nuances of ERP Cloud User Access Control truly began.
I remember one particular project manager, let’s call her Sarah, who was initially a bit dismissive. "Why can’t everyone just have full access? We’re a team!" she’d say. It was a common sentiment, born from a desire for seamless collaboration. But I had to explain to Sarah, with patient analogies, that it wasn’t about distrust, but about responsibility and risk. Giving everyone the keys to the entire city might sound collaborative, but what happens when someone accidentally deletes a critical customer database? Or, worse, intentionally diverts funds? The potential for error, fraud, and data breaches skyrockets. This is why robust ERP Cloud security isn’t just a technical requirement; it’s a business imperative.
One of the foundational principles we hammered home was the concept of Least Privilege. This means giving users only the permissions absolutely necessary to perform their job functions – no more, no less. It’s like a chef in a restaurant. They need access to the kitchen, the pantry, and their specific workstation. They don’t need keys to the safe where the daily takings are stored, nor access to the HR manager’s office. Applying this to Cloud ERP means a sales representative might be able to view customer orders and create new ones, but they shouldn’t be able to approve large financial transactions or modify employee payroll data. This principle significantly reduces the "blast radius" if an account is compromised or if an employee makes an honest mistake.
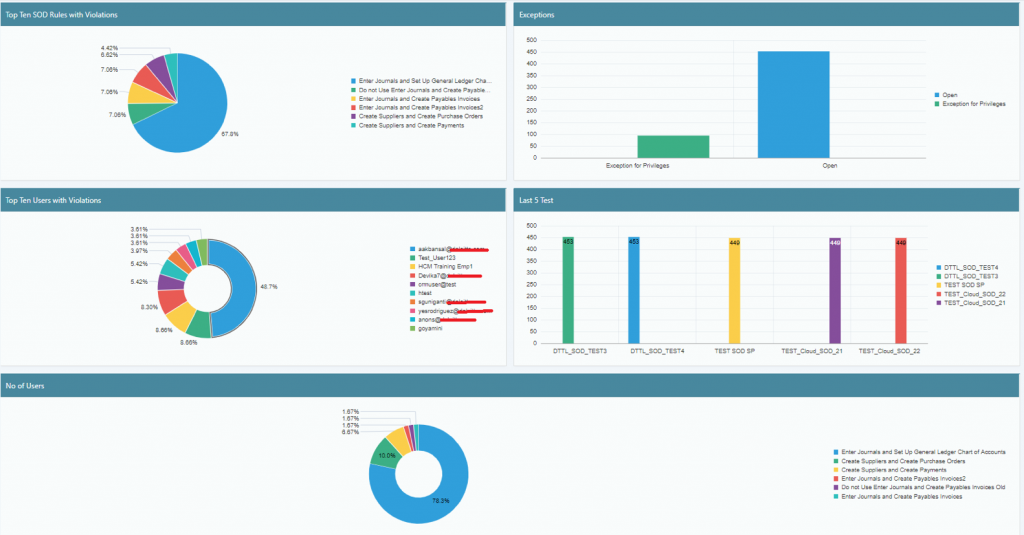
Closely related to Least Privilege, and equally vital, is Segregation of Duties (SoD). This was a tough one for some smaller teams to grasp, as it often meant splitting tasks that one person used to handle. SoD is about ensuring that no single individual has control over an entire critical process from start to finish. Think about the classic example: the person who creates a purchase order should not be the same person who approves the payment for that order. Why? Because it prevents opportunities for fraud. If one person can both order something and pay for it, they could order goods for personal use and approve their own payment. In our Cloud ERP, we meticulously mapped out business processes and identified potential SoD conflicts, then designed roles and permissions to ensure that these checks and balances were in place. It was a painstaking process, but absolutely essential for maintaining financial integrity and compliance.
This brings us to Role-Based Access Control (RBAC), which became our primary tool for implementing these principles. Instead of assigning individual permissions to each user (imagine the nightmare of managing that for hundreds or thousands of employees!), we created roles. A "Financial Analyst" role, for example, would have a predefined set of permissions related to financial reporting and analysis. A "Procurement Specialist" role would have permissions for creating purchase requisitions and managing vendor information. When a new employee joined, or an existing one changed departments, we simply assigned or updated their role, and all the relevant permissions came with it. This simplified user access management immensely, making it scalable and much less prone to human error. It was like having a set of pre-configured access cards for different parts of our digital city.
Of course, identity itself is paramount. This is where Identity and Access Management (IAM) comes into play, though it’s a broader discipline. Within our Cloud ERP context, it meant ensuring that we knew who was trying to access the system. We implemented Multi-Factor Authentication (MFA) across the board. Gone were the days when a simple password was enough. Now, logging in required something you knew (your password) and something you had (a code from your phone or a hardware token). This single step, though sometimes a minor inconvenience for users, provided an enormous leap in security, making it vastly harder for unauthorized individuals to gain access, even if they somehow managed to steal a password. I’ve seen firsthand how MFA has thwarted potential breaches, and I can’t stress its importance enough.
Our journey wasn’t without its bumps. One of the biggest challenges was the sheer complexity. Modern Cloud ERP systems are incredibly powerful, with thousands of potential permissions and configurations. Mapping these to real-world job functions and ensuring no gaps or overlaps required deep collaboration between our IT team, HR, finance, and other business units. It wasn’t just a technical exercise; it was an organizational one. We spent countless hours in workshops, drawing diagrams on whiteboards, trying to visualize how different roles would interact with the system and what level of access they truly needed. It felt like designing a super-intricate clockwork mechanism where every gear had to mesh perfectly.
Another hurdle was managing the user lifecycle. People join, change roles, or leave the company. Each of these events triggers a need to update their access. If an employee changes departments, their old permissions might become inappropriate or, worse, a security risk if they retain access to sensitive data from their previous role. If someone leaves, their access must be revoked immediately. Automating these processes where possible, and establishing clear, documented procedures for manual changes, became crucial. We learned the hard way that a single oversight in offboarding could leave a lingering vulnerability.
Compliance, too, was a constant companion. Depending on the industry and geographic location, various regulations like GDPR, SOX, HIPAA, or local data privacy laws dictate how sensitive information must be handled and who can access it. Our ERP Cloud user access controls had to be auditable, meaning we needed clear records of who had access to what, when, and why. This wasn’t just about avoiding fines; it was about building and maintaining trust with our customers and stakeholders. Regular audits became a non-negotiable part of our routine, helping us to identify and rectify any deviations from our policies.
So, how did we navigate this complex terrain? We adopted several best practices that I now preach like gospel.
First, start with a clear strategy. Don’t just dive in. Define your organization’s security posture, identify your most sensitive data, and understand your regulatory obligations. This strategic foundation guides all subsequent decisions regarding access control. We began by asking: "What are we trying to protect, from whom, and why?"
Second, involve business stakeholders from the outset. IT can build the gates and walls, but only the business units truly understand who needs to walk through which doors to do their jobs. Their input is invaluable for defining roles, identifying SoD conflicts, and ensuring that the access controls don’t hinder productivity. It’s a collaborative effort, not an IT mandate.
Third, document everything. Every role definition, every permission assigned, every change made – it all needs to be documented. This documentation serves multiple purposes: it acts as a reference for new team members, provides evidence for auditors, and helps in troubleshooting access issues. It’s the instruction manual for our digital city.
Fourth, train your users. Even the most perfectly designed access control system can be undermined by human error or ignorance. Educate users on the importance of strong passwords, the dangers of phishing, and why certain access restrictions are in place. When users understand why security measures exist, they are more likely to comply and become part of the solution rather than a potential weak link.
Fifth, automate where possible, but review regularly. Tools for automated provisioning and de-provisioning users, or for identifying SoD conflicts, can be incredibly helpful. However, don’t set it and forget it. Business processes evolve, job functions change, and new threats emerge. Regular reviews, perhaps quarterly or bi-annually, are essential to ensure that access controls remain aligned with the organization’s needs and current security landscape. I found that having a dedicated team member responsible for "access governance" helped immensely.
Sixth, understand your cloud vendor’s security model. When your ERP is in the cloud, you’re sharing responsibility for security with your provider. They manage the security of the cloud (the infrastructure, the underlying platform), while you’re responsible for security in the cloud (your data, your configurations, and critically, your user access controls). Knowing where their responsibility ends and yours begins is crucial for a complete security posture. It’s like living in an apartment building: the landlord secures the building, but you secure your apartment door.
Finally, remember the human element. Technology is a powerful enabler, but people are at the heart of any security strategy. A culture of security, where everyone understands their role in protecting company data, is perhaps the strongest defense you can build. It’s about fostering awareness, promoting ethical behavior, and ensuring that security isn’t seen as a barrier, but as a fundamental aspect of doing business responsibly.
Looking ahead, I see even more exciting, and perhaps daunting, developments in ERP Cloud user access control. The rise of AI and machine learning promises more intelligent access decisions, potentially identifying unusual behavior or automatically suggesting appropriate permissions based on job roles and historical activity. Zero-trust models, where no user or device is inherently trusted, regardless of whether they are inside or outside the network, are gaining traction, pushing us towards even more granular and continuous verification.
My journey with ERP Cloud user access control has taught me that it’s not a static project with a defined end. It’s an ongoing, dynamic process, a constant balancing act between enabling business operations and protecting valuable assets. It requires vigilance, collaboration, and a deep understanding of both technology and human behavior. It’s about building a digital city where everyone can move freely to do their work, but where the right gates, the right keys, and the right guardians ensure that chaos never takes hold. And in this ever-evolving digital landscape, mastering this intricate dance is not just good practice; it’s the very foundation of trust and success.